Being Dangerous Online: Analyzing an Ongoing Phishing Campaign in Belgium and the Netherlands
Introduction
An acquaintance of mine pointed me towards a phishing campaign their family member had fallen for. Thankfully, after communicating with the bank, the stolen amount (upwards of 2,000 Euros) was recovered. However, the campaign that lead to that theft was still up. For the sake of public safety and knowledge, it’s important to share this campaign’s techniques, as I have to say, there is a degree of novelty and sophistication to it.
The Bait
The scammers in this case advertised cheap tickets for the ‘70th’ birthday of ‘Efteling’ a famous amusement park.
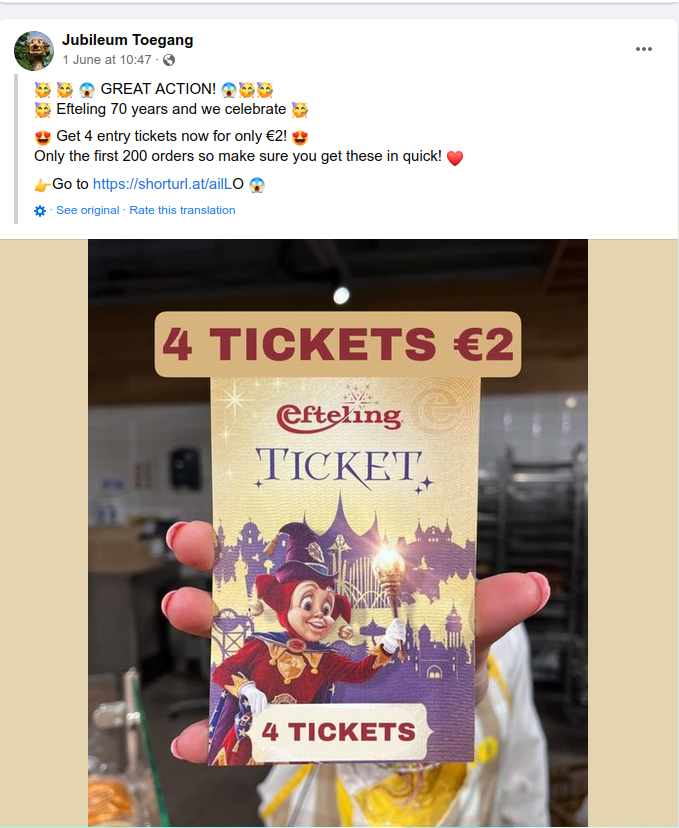
Following the link, we are then taken to a relatively legitimate looking payment portal. This is not yet where the phishing actually happens, as to some degree the first payment portals the scammers link you to is this:
<span>https://876073.myshopify.com/products/efteling-jubileum-tickets</span>
Although a little dodgy with the numerical subdomain, never the less, myshopify is a legitimate e-commerce website and could fool detection systems as an initial link.
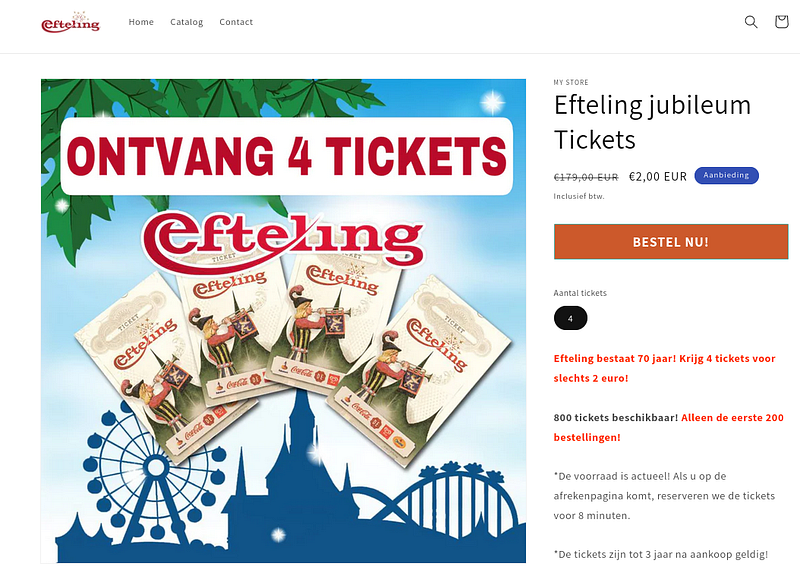
Clicking on the large orange ‘ORDER NOW!’ button leads us to the real phishing portal.
The Phish
The website itself is actually quite convincing and has similar attributes to many legitimate payment portals that victims have surely used before. However, it’s important to note the URL of this website:
s1gnupn0w(.)net/c/xxxxxxxxx
This URL seems to be owned by the attackers and serves as a ‘landing’ page of sorts.
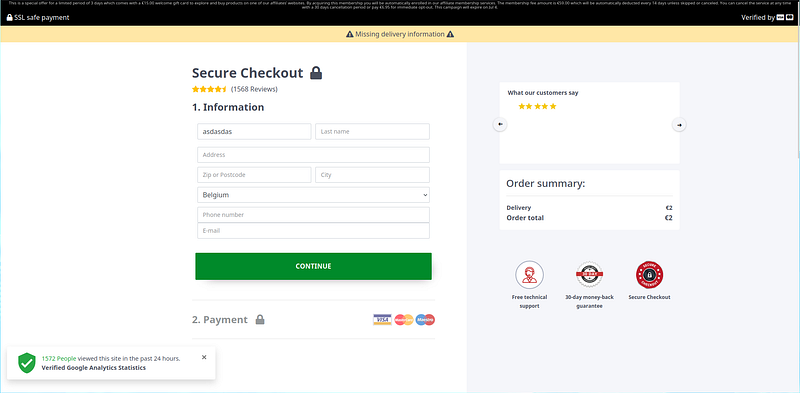
Filling in that information, we are then taken to yet another website, this time, however, on what seems to be a hacked TV website which I will not share the URL of for their own safety:
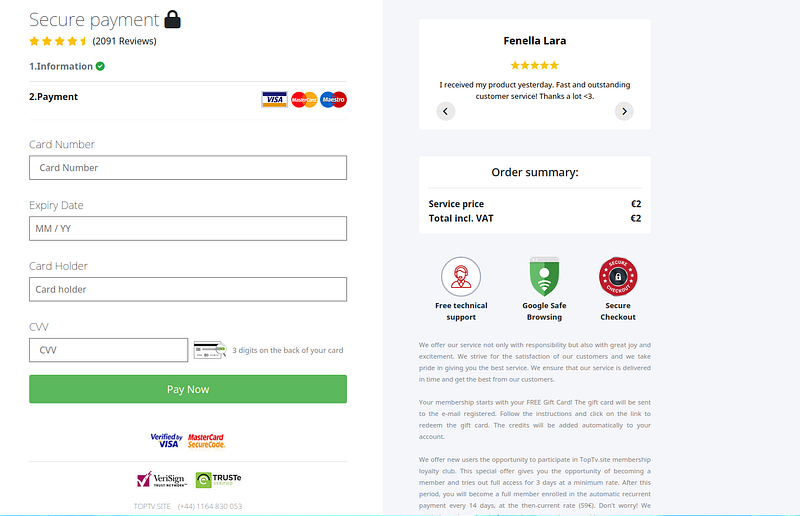
After entering their information, the victims had the expected two euros taken from them, and then a singular large sum a few short minutes after that.
The Tell-Tale Signs
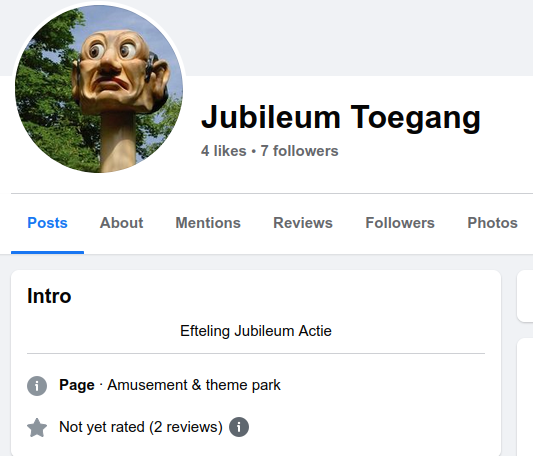
This is undoubtedly a very sophisticated campaign with proven former success. We can learn more about the campaign and perhaps the scammers by observing them a bit closer. By looking exactly who is advertising this, we can begin seeing the hallmarks of a phishing campaign. Let’s take a look at the original ad and deconstruct its elements:
- ) The advertisement was posted by an account with very few followers
2.) The campaign uses shorturl.at (or some variant like bit.ly or is.gd) to obfuscate their links and escape detection.
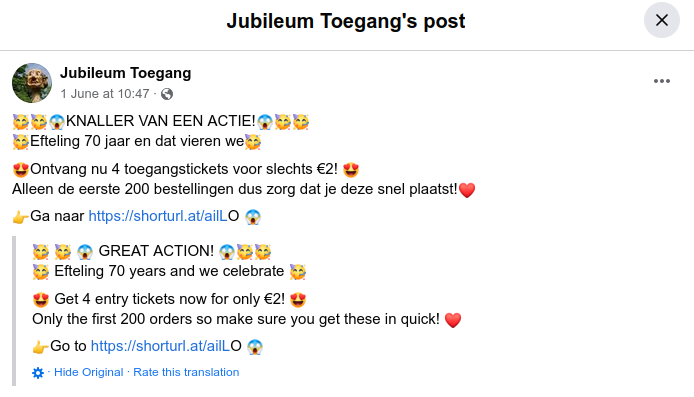
3.) A sense of urgency by marketing it as something only the first 200 orders can participate in.
4.) This is what I think makes these scammers sophisticated, is that they managed to create a set of fake accounts which they use to comment on their advertisement to add validity.
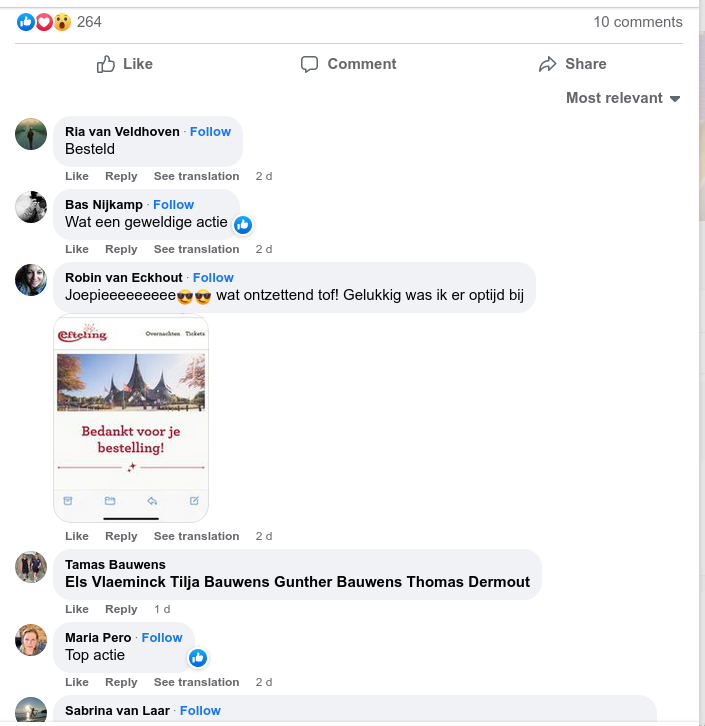
The way I found out that many of these accounts are fake was by clicking through them and seeing patterns. For example, many of the accounts included a url in their bio which led nowhere. Some examples here:
The Bad News
The scammers have been successful before. This is obviously not their first time around. Looking further into that account, I found an earlier phishing campaign similar to this one that seems to have found a relative degree of success with many legitimate accounts posting gleefully about the deal they made.
The Good News
The account has been reported, and I’m looking for the right channels to communicate with to somehow stop the accounts associated with this attack. I recommend you add these URL’s into any blocklists you have running at the very least, and make sure you inform the parties you are responsible over about this on-going attack in Belgium and the Netherlands.