A Home Lab Odyssey: Maximizing a Second-Hand HP Z400
Introduction
As security researchers, we are constantly under threat. The nature of our curiosities lead us down dark cyber paths that require meticulous processes to come out of unnoticed. Additionally, for those who dig deeply into malware and criminal activity online, that requirement becomes central for safety. Accordingly, a seasoned security researcher ought to have the defenses in place that keep them safe from intruders or even more likely, mistakes!
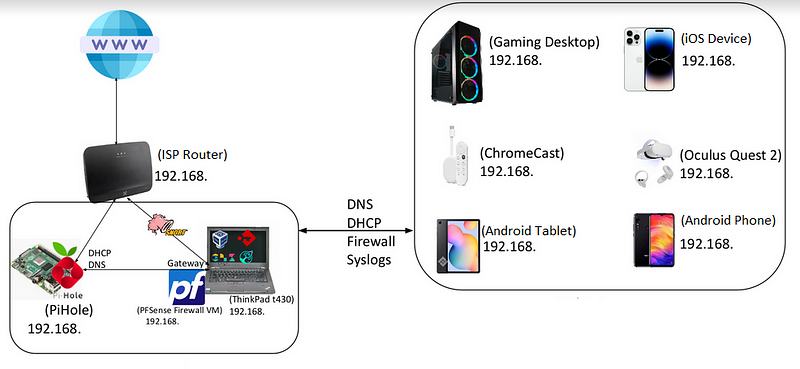
My initial set-up to maintain my defenses at home was modest, but robust. It ran entirely on a Raspberry pi and a Thinkpad T430, which ran on an i5 processor with 12GB of ram and 250GB of space. However, having only one network card limited my expansion of that device, plateauing at a few network functions; primarily DNS filtering, DHCP, fire-walling, IDS/IPS and a sometimes functional Splunk SIEM (This was a ram hog, hardly possible on 12GB), so I opted for a free cloud Grafana instance, now on the path to be replaced by Wazuh.
But it wasn’t long before I found a fixer-upper that caught my eye that could fulfill many more of my required use-cases, and an upgrade was born.
1.) The Hardware
1.1) The HP Z400 Workstation
The cornerstone of my home lab upgrade was the acquisition of a second-hand HP Z400 Workstation. This workstation, though older, possessed the potential to significantly enhance my home defense setup. Let’s delve into its specifications and capabilities:

- Processor: Initially, the HP Z400 came with a powerful processor, allowing for resource-intensive tasks often encountered in security research. However, recognizing the need for even more processing power, I upgraded the processor to a 6-core, 12-thread Intel X5670, which I managed to acquire for the incredible price of just 8 euros. This upgrade would turbocharge the workstation’s capabilities, enabling it to handle the most demanding research tasks with ease.
- RAM: Finding the right RAM for the HP Z400 was a challenging task. ECC (Error-Correcting Code) RAM is crucial for maintaining data integrity in a security research environment. I searched extensively, and this proved to be the hardest part of the upgrade. In my local market, all available ECC RAM was buffered, which wasn’t compatible with the Z400. After a persistent search, I finally located ECC Unbuffered RAM modules that were compatible with the workstation. This discovery was a turning point, as it allowed me to ensure data reliability in my research environment. Quickly, I bought myself 4x8GB sticks of ECC Unbuffered DDR3 ram
- BIOS Upgrade: The HP Z400’s documentation stated that it could handle a maximum of 24GB of RAM. However, I was determined to push its limits further. After some research, I discovered that a BIOS upgrade could potentially unlock additional memory capacity. With some trepidation, I performed the BIOS upgrade, and to my delight, it allowed the workstation to handle up to 48GB of RAM. This was a significant boost to its capabilities and provided the necessary headroom for my resource-intensive research tasks.
- Expansion Slots: The HP Z400 featured multiple expansion slots, which would prove invaluable for adding additional network cards and storage options. This expandability would eliminate the limitations I faced with my previous setup, allowing for a broader range of network functions and storage solutions.
The HP Z400 Workstation, now equipped with the upgraded 6-core, 12-thread Intel X5670 processor and expanded to 32GB of ECC Unbuffered RAM (thanks to a BIOS upgrade), was the ideal candidate to enhance my home lab’s capabilities.
2.) The Software
2.1 Introduction to Proxmox

With the HP Z400 Workstation serving as the backbone of my upgraded home lab, the next step in my journey was to implement a robust hypervisor to maximize the workstation’s capabilities. After thorough research and consideration, I chose to install Proxmox Virtual Environment (Proxmox VE) as my hypervisor of choice.
Proxmox VE is an open-source virtualization platform that combines two powerful virtualization technologies: KVM (Kernel-based Virtual Machine) for virtual machines (VMs) and LXC (Linux Containers) for lightweight container-based virtualization. Here’s why Proxmox VE was the ideal choice for my home lab:
- KVM Virtualization: Proxmox VE’s use of KVM allowed me to create and manage virtual machines with excellent performance and hardware-level virtualization support. This was crucial for running various security research tools and simulations within isolated VMs.
- LXC Containers: LXC containers provided a lightweight and efficient means of virtualization for applications and services that required less resource overhead. It allowed me to run multiple isolated workloads on a single physical server. These are similar to docker containers.
- Web-Based Management Interface: Proxmox VE’s web-based management interface made it user-friendly and accessible. I could easily create, configure, and monitor VMs and containers through a convenient web portal.
2.2 Virtualizing pfSense
One of the primary use-cases for my upgraded home lab was to create a secure and customizable network environment. For this purpose, I decided to virtualize pfSense, a powerful open-source firewall and routing platform. With Proxmox VE, I could allocate dedicated resources to pfSense, ensuring optimal performance. Here’s how I set it up:
- pfSense VM: I created a dedicated virtual machine for pfSense and allocated it two of the workstation’s network interfaces, thanks to the NIC PCIe card upgrade. This allowed me to set up a dedicated WAN and LAN interface, ensuring that traffic was properly segmented and controlled.
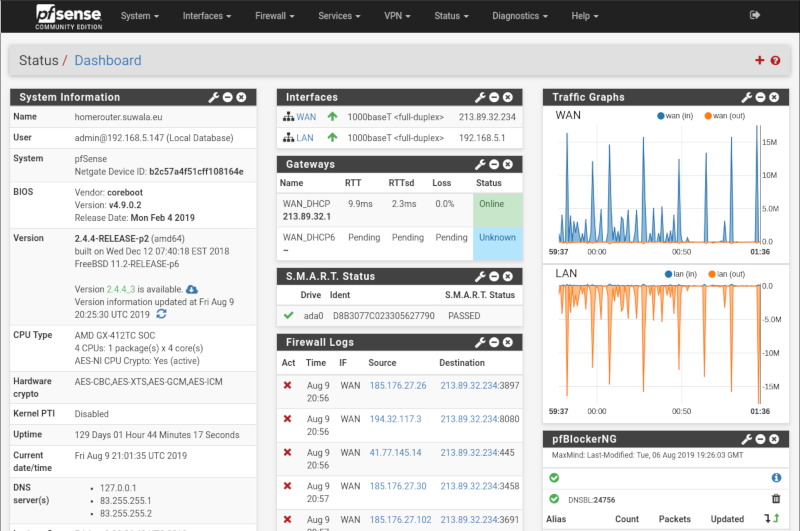
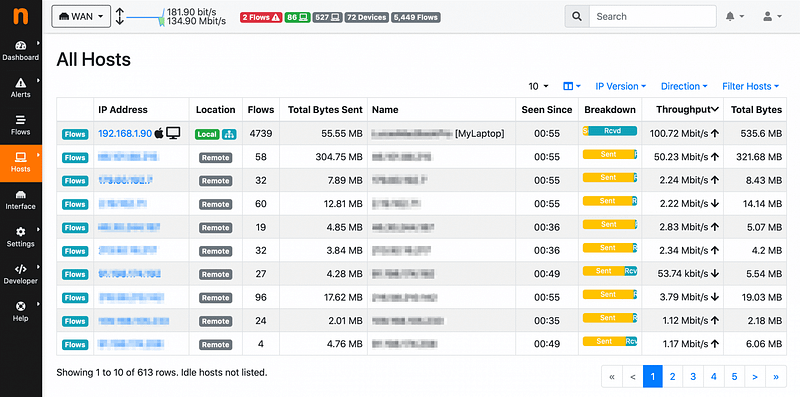
- ntopng: To monitor network traffic and gain insights into network activity, I also set up ntopng as a pfSense plugin. ntopng provided detailed network analytics, helping me detect any unusual or suspicious network behavior.
- Snort: To enhance security, I implemented Snort, an open-source intrusion detection system (IDS) as a pfSense plugin. Snort actively monitored network traffic for potential threats and provided alerts when suspicious activity was detected.
2.3 Virtualizing Pi-hole and PassBolt
In addition to securing my network, I also aimed to enhance privacy and productivity within my home lab environment. To achieve this, I virtualized two essential services:
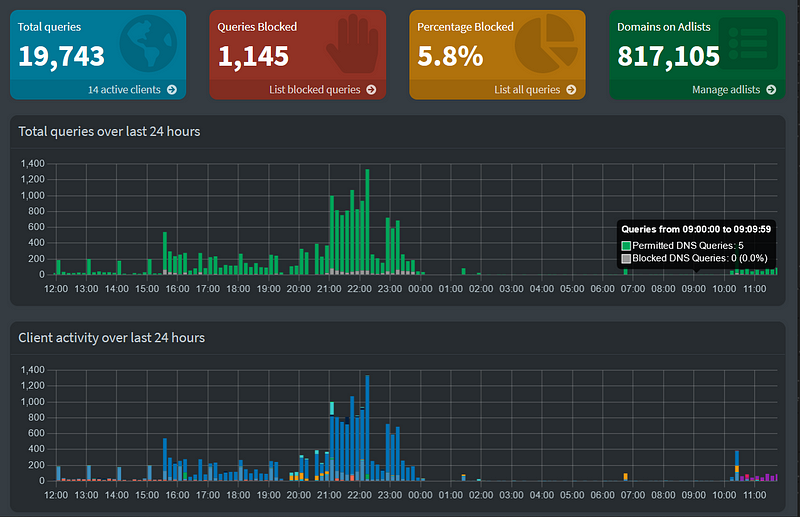
- Pi-hole: I created a Pi-hole virtual machine to serve as a network-wide ad blocker and DNS sinkhole. Pi-hole blocked unwanted advertisements at the network level, resulting in a cleaner and more efficient browsing experience while also enhancing privacy.
- PassBolt: For secure password management and collaboration, I set up PassBolt, an open-source password manager. PassBolt allowed me to securely store and share passwords with team members or securely access them when needed.
With Proxmox VE as the foundation of my virtualized home lab, I could easily manage and scale these services, ensuring that my network was not only secure but also optimized for productivity and privacy.
2.4 Virtualizing Operating Systems for Security Research and Penetration Testing
I recognized the need for a versatile environment to facilitate learning and testing various operating systems and security scenarios (and a justification for the unholy amounts of ram I’ve invested in). Proxmox VE proved to be the ideal platform for this purpose, enabling the virtualization of multiple operating systems to meet diverse security and privacy requirements.
Kali Linux: To explore and experiment with the latest penetration testing tools and techniques, I created a dedicated Kali Linux virtual machine. This allowed me to conduct ethical hacking exercises, vulnerability assessments, and security audits within a controlled environment.
Windows: The need for a Windows environment for compatibility testing and analysis was paramount. Through Proxmox VE, I provisioned a Windows virtual machine, offering a versatile space to assess software, examine security configurations, and explore the intricacies of Windows-based attacks and defenses.
Whonix Gateway and Deep Web VM: Recognizing the importance of anonymity and privacy in certain research endeavors, I introduced the Whonix Gateway into my lab setup. This dedicated gateway, coupled with a virtual machine designed for deep web exploration, provided me with a secure and anonymized environment for navigating the onion network and wider clear-net.
Vulnerabe Machines: As a security researcher, hands-on experience with real-world vulnerabilities is invaluable. By downloading images from https://www.vulnhub.com/ I can set up a series of dedicated vulnerability machines, each hosting specific challenges and exploits for testing and skill enhancement. This dynamic environment enables me to sharpen my understanding of vulnerabilities and practice responsible disclosure.
I can go on and on about the technologies this enables. With Proxmox VE’s flexibility and robust management capabilities, I could effortlessly create, clone, and manage these virtualized operating systems, tailoring my lab environment to suit each unique learning and testing scenario. This versatility not only enriched my knowledge but also empowered me to adapt and respond effectively to the ever-evolving landscape of cybersecurity challenges.
3.) Network Setup
TP-Link TL-WA801ND
In my quest for a highly organized and secure network environment, I embarked on a journey to enhance my network infrastructure. To achieve this goal, I made the strategic decision to install OpenWRT on my TP-Link TL-WA801ND, a pivotal component of my network setup. This transformation was instrumental in taking my network to the next level of customization and security.
Device Selection and Importance: The TP-Link TL-WA801ND, known for its reliability and versatility, was chosen as a cornerstone of my network architecture. Its selection was based on its ability to handle OpenWRT, an open-source firmware known for its advanced features and robust security options. With this device in place, I was ready to create a network environment tailored to my specific needs.
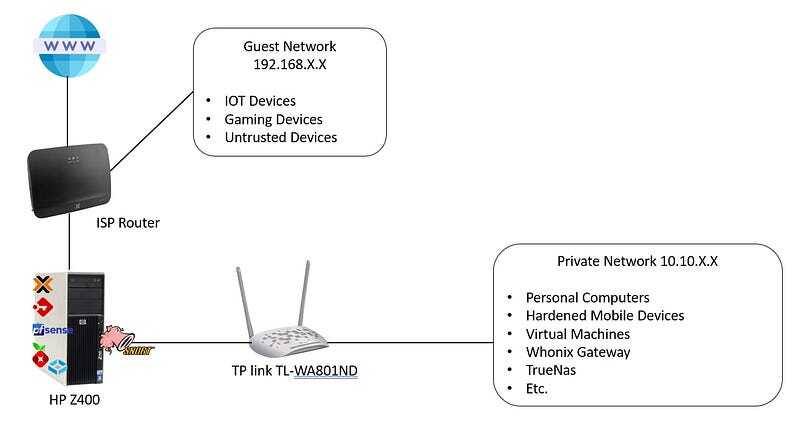
Segregation for Enhanced Security: One of the primary objectives of this upgrade was to establish a segregated VLAN (Virtual Local Area Network) dedicated exclusively to guest and untrusted devices. This deliberate segregation was implemented to maintain the integrity and security of my primary network. By isolating these devices in a separate VLAN, I could ensure that any potential threats or breaches would be contained, preventing them from affecting my core network.
Role of pfSense in Network Security: To further fortify my network’s defensive capabilities, I had meticulously configured pfSense, a powerful open-source firewall and routing platform. This robust software was entrusted with the critical task of monitoring and protecting the newly created secondary network, where guest and untrusted devices resided. PfSense’s advanced features and intrusion detection capabilities allowed me to keep a vigilant eye on this segregated network, promptly identifying and mitigating any security risks that might emerge.
Conclusion
My home lab odyssey began with a modest yet resilient setup, anchored by my trusty Lenovo T430 laptop. However, the limitations of a single network card prompted me to seek a more versatile solution. It wasn’t long before my quest led me to the remarkable HP Z400 Workstation, a second-hand gem brimming with untapped potential.
Future Upgrades
As my home lab continues to evolve, several upgrades are under consideration:
- TrueNas: A popular storage solution that offers robust data management and protection capabilities. TrueNAS supports a variety of RAID configurations, including RAID 5, which will be essential to maintain backups and availability of my personal and research data in a TrueNAS system.
- Wazuh: The implementation of Wazuh, an open-source security monitoring platform, is in the pipeline. It will add an extra layer of security vigilance to my lab environment.
- GPU Passthrough and Virtual Gaming: To minimize electricity costs and maximize efficiency, GPU passthrough for virtual gaming is under evaluation. This would allow gaming within virtual machines, reducing the need for dedicated gaming rigs.
In the ever-evolving landscape of security research, adaptability and continuous improvement are imperative. My home lab is an ongoing project of fortifying defenses, expanding capabilities, and enabling experimentation safely within a safe-guarded environment.