Automating Bug Bounty Recon: Creating the Flask API
The initial reconnaissance phase in a bug bounty program can be the difference between finding a critical vulnerability and missing it altogether. Automation, when thoughtfully implemented, can significantly enhance the efficiency of this phase. In my Flask API, I have methodically automated several crucial recon tasks, ensuring a comprehensive and organized approach. This article will delve deep into the API’s functionality and the sequence of operations it undertakes.

1. Passive Reconnaissance: Establishing the Foundation
Upon triggering the /passive-recon/<domain> endpoint, a systematic passive recon process is initiated:
Subdomain Enumeration with Sublist3r, crt.sh, and Amass
The very first step is enumerating all possible subdomains of the given domain. For this purpose, a combination of tools is employed:
- Sublist3r: An open-source tool that scours a multitude of sources, from search engines to SSL certificates, aiming to uncover every conceivable subdomain.
- crt.sh: A certificate search engine that taps into the vast database of certificate logs, highlighting subdomains associated with SSL certificates.
- Amass: An advanced tool that goes beyond simple subdomain enumeration. By using passive sources, web scrapers, and even brute forcing, it ensures a holistic discovery of subdomains.
Alive Subdomains Validation with HTTPX
Once the subdomains are enumerated, HTTPX is employed to check which ones are alive. During this phase, it also validates if the subdomains are accessible via http, https, or both, ensuring a comprehensive scan.
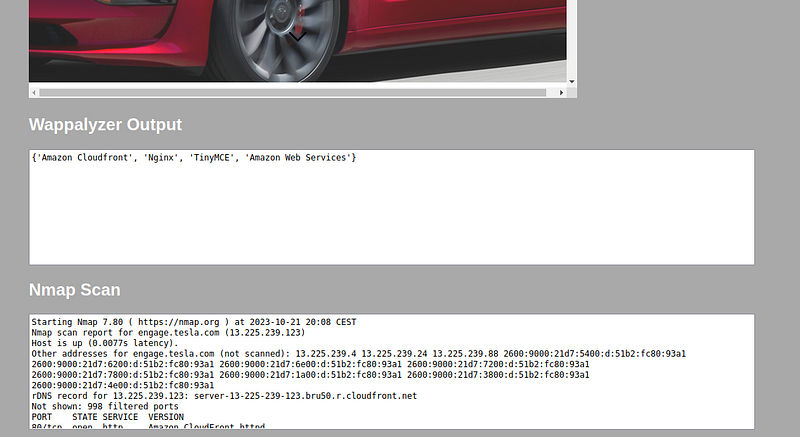
Technology Stack Analysis using Wappalyzer
For every live subdomain, Wappalyzer identifies the underlying technology stack. This information can later inform specific testing methodologies based on known vulnerabilities of certain technologies.
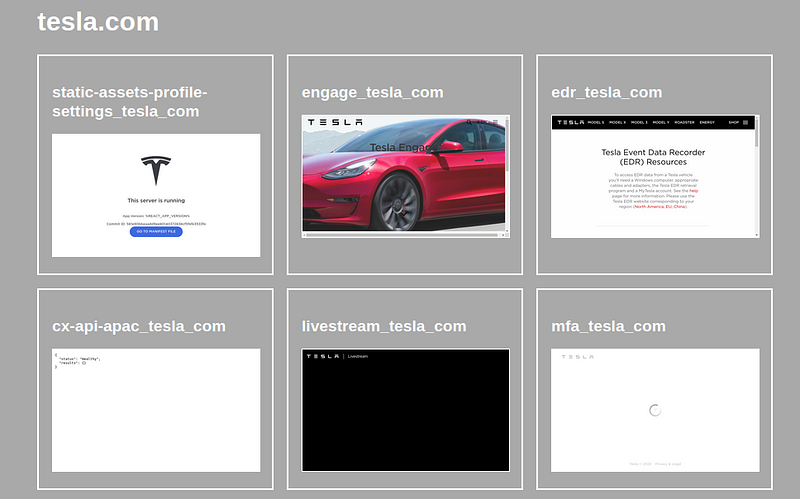
Capturing Visual Insights with Selenium
Selenium then steps in to take screenshots of these subdomains. These visual aids not only provide a quick snapshot of the webpage’s layout and content but also become invaluable assets during the manual review phase.
Organized Data Presentation in Flask
Finally, all this information is methodically organized and made accessible via Flask, presenting researchers with a structured dataset ready for analysis.
2. Active Reconnaissance: Digging Deeper
Upon a successful passive recon, the /active-recon/<domain> endpoint can be invoked to dive deeper:
Web Crawling with GoSpider
GoSpider crawls the identified subdomains, mapping out the web structure and extracting links. This ensures no endpoint, hidden or overt, goes unnoticed.
Historical Data Retrieval using Waybackpy
The waybackpy tool fetches historical data of the subdomains. This is crucial as it can uncover 'ghost endpoints' — old or forgotten URLs that developers might have overlooked. These endpoints, although not active, can sometimes still be accessed and might contain vulnerabilities.
Extracting URLs with Parameters
All URLs with parameters are then extracted. The parameters are replaced with placeholder values using qsreplace, prepping them for potential payload injection during vulnerability scans.
3. Vulnerability Scans: Identifying Weak Spots
Initiating the /vulnerability-scan/<domain> endpoint embarks on a quest to identify vulnerabilities:
Targeted Scans with kxss and SQLMap
Quick scans are run on the URLs using tools like kxss for potential cross-site scripting vulnerabilities and sqlmap for possible SQL injection points.
Comprehensive Port Scanning with Nmap
Nmap then conducts a thorough scan on all ports of the subdomains, identifying open ports and the services running on them.
Contemplating Nikto for Automation
Currently, we’re assessing the feasibility of integrating Nikto into the automation pipeline. Given its prowess in web server scanning, if paired intelligently with the outputs from Wappalyzer, it could offer more targeted and efficient scans, especially when paired with custom templates.
Closing Thoughts
Automation in bug bounty recon doesn’t eliminate the need for manual testing but augments it. By handling repetitive tasks and organizing data coherently, it allows researchers to focus their expertise on in-depth analysis. As the digital realm continues to grow, tools and methodologies like these will be paramount in ensuring its security.